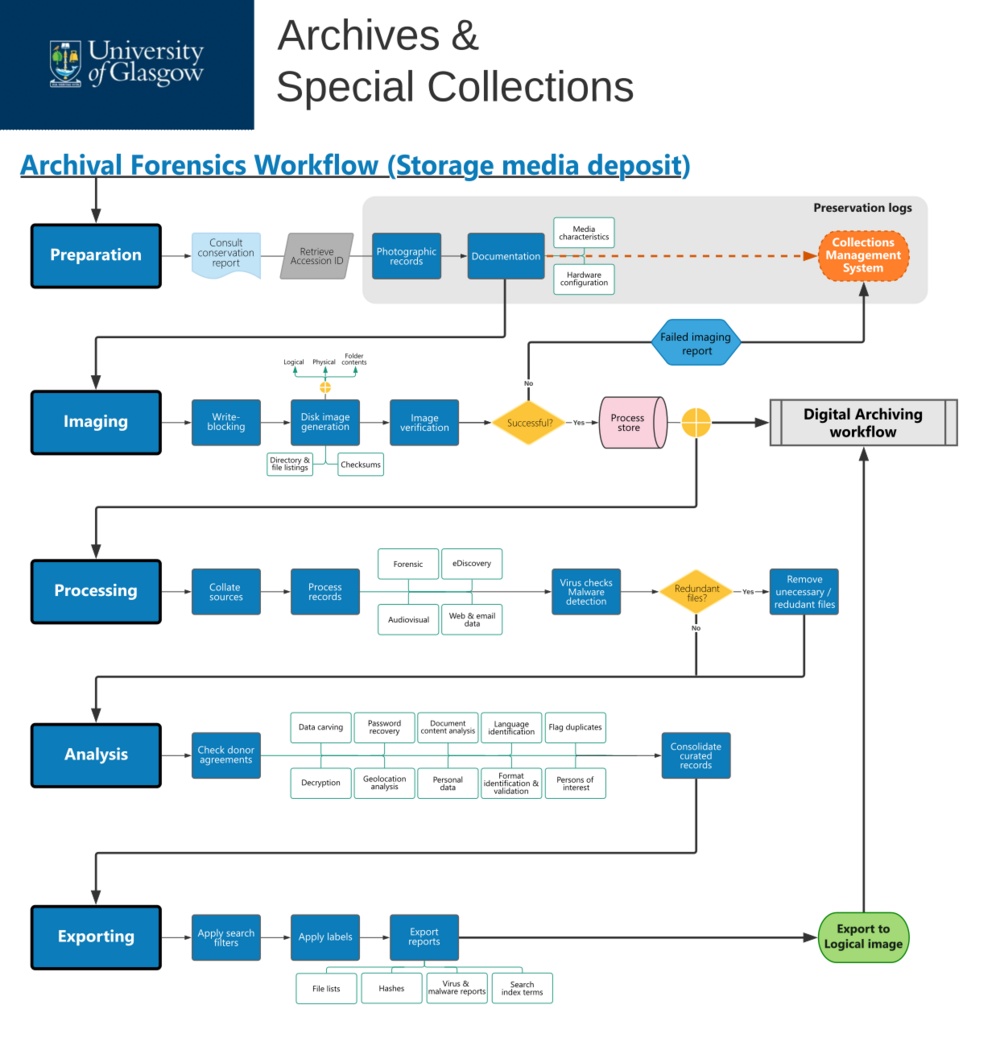
Workflow:Archival Forensics workflow (storage media deposit)
Jump to navigation
Jump to search
Workflow Description[edit]
- START
- A request to forensically process a digital deposit (storage media) to the University of Glasgow Archives & Special Collections, as part of of the Digital Archiving workflow.
- PREPARATION
- Obtain supporting resources and materials to forensically process digital storage media.
- Consult the physical conservation and preservation report, documenting all actions on the acquired media and produced during Acquisition in the Digital Archiving workflow.
- Retrieve the unique accession number generated for the media to be processed from the Collections Management System. Use the accession number as reference in all forensic processing actions.
- Update the conservation and preservation logs on the Collections Management System relating to the storage media, including:
- photographic records of the storage media before processing, clearly showing state, serial number(s) and any other relevant information recorded on the media (e.g. labels).
- Documentation of media characteristics, such as technology, type, brand, model, serial number.
- Documentation of any hardware setup or configuration necessary to process the storage medium.
- Proceed to Imaging.
- IMAGING
- Create an exact copy of storage media, encapsulating contents and structures in a single file (a disk image).
- Use write-blocking tools (software or hardware) to only permit read-only access to storage media, so as to avoid compromising the integrity of the data; and protect the data chain of custody.
- Use disk imaging software to generate a forensic image file, which can either be:
- a physical image, which is a bit-by-bit (exact) copy of the storage medium and includes active (used) and free space. Any deleted data or file fragments will be copied into the image file.
- A logical image, which captures active data on the device but not any deleted space, deleted files or fragments.
- A selection of specific files and directories, also known as a targeted collection.
- Instruct the disk imaging software to create a complete file and directory listing; and verify the integrity of the generated image file by comparing hashes:
- If verification fails and attempts at re-imaging are unsuccessful, create a "failed imaging" report in the Collections Management System logs.
- If verification is successful, store the image in process store.
- Is further forensic processing and analysis required?
- If no, submit the verified disk image to the Digital Archiving workflow. OR
- If yes, proceed to Processing.
- PROCESSING
- Extract and manage information from the data in storage media, and make it available for analysis.
- Collate sources for processing, by selecting specific folders/files to review and - where appropriate - aggregating data from multiple storage media.
- Perform virus and malware detection checks on the collated sources.
- Use forensic software to identify and, if possible, remove irrelevant or redundant files from processing. Examples may include operating systems, system files, or user-defined files that have been deemed as irrelevant.
- Use forensic software to process the data, including hash generation for files; expanding compound files (e.g. zip archives); format identification and validation; creating search text indices; and preparing audiovisual, web and email data for analysis.
- Proceed to Analysis.
- ANALYSIS
- Use digital forensics methods to search, categorise, review, interpret and curate data in storage media, so as to aid selection and appraisal processes.
- Review the agreement(s) under which the records were donated, in order to identify permissible actions (e.g. whether restoring deleted files is allowed).
- Depending on the nature of the data and on archival needs, use forensic software to identify records of interest, and make them available for appraisal. Analysis methods may include:
- Data carving, for restoring data that was deleted or lost from the file system.
- Decrypting encrypted files and recovering passwords for password-protected files.
- Viewing and exporting geolocation data from files that have geolocation information associated with them.
- Analysing document content to explore terms/words of interest; and automate the identification of personal information, such as names, phone numbers, credit card and social security numbers.
- Identifying the language in which documents are written.
- Generating thumbnails from images and videos; and extracting metadata from multimedia files.
- Flagging duplicate files.
- Discovering information (including documents and email communications) relating to pre-defined lists of persons of interest.
- Once all analyses have been completed, consolidate the resulting data into an appropriate file/folder structure.
- Proceed to Exporting.
- EXPORTING
- Export the forensically analysed contents of storage media as logical disk images, alongside relevant processing reports, filters and labels.
- Export any custom filters and labels created to manage the data, which can be useful for other digital archiving processes. Filters help locate items of interest quickly; and labels allow for grouping files in customised ways (e.g. flagging content that requires archivist attention; or records associated with a specific individual).
- Export any reports generated during processing and analysis, such as file hashes, virus and malware detection reports, search index terms and geolocation data.
- Export the forensically curated contents of processed storage media into a logical disk image.
- Submit the logical disk image to the Digital Archiving workflow.
Purpose, Context and Content[edit]
The workflow is meant to describe the steps and processes involved in an archival forensics examination of digital records submitted in storage media to University Archives at the University of Glasgow. Although the workflow can operate as stand-alone, it has been designed to align with and extend the Digital Archiving workflow.
Further Information[edit]
- Digital Preservation policy, University of Glasgow
- Digital Archiving workflow, University of Glasgow
- Digital preservation workflows, The National Archives
Leo Konstantelos (talk) 12:13, 26 May 2023 (UTC)